Do-It-Yourself Data Recovery
Updated for 2019…I have an all new DIY process built to automate data recovery from failed RAID/NAS devices. It’s called NASmatic and is very easy to use. It is based on the experience gained from years of NAS / RAID data recovery work. If you would like to give it a try read the NASmatic Quick Start Guide.
RAIDfinder is still operational but NASmatic is much easier and has many improvements. For RAIDfinder info read on. (Or scroll down for single drive DIY recovery info.)
R A I D f i n d e r
R A I D / N A S D a t a R e c o v e r y M a d e E a s y
RAIDfinder Quick Start:
- Connect your RAID member drives to SATA ports on a desktop computer.
- Download the RAIDfinder .iso file, size 312MB…FDR-5848G-RAIDfinder.iso
- Either burn the .iso to make a boot CD or make a bootable USB thumb drive with Rufus… http://rufus.ie/
- Boot the desktop computer with the CD or USB drive. Boot time is 3 to 5 minutes.
- From another computer open Windows Explorer and navigate to the network share RAIDfinder displays on screen, for example \\192.168.1.88
- Help RAIDfinder learn about your RAID. Edit the helper file in notepad and identify your RAID member drives.
- That’s it. Standby as RAIDfinder automatically begins a search for your RAID data
Introduction:
RAIDfinder automates the data recovery process for failed RAID0, RAID1, RAID5 and RAID6 storage devices. It’s based on the experience gained from hundreds of remote recovery cases performed over the last few years. RAIDfinder operates from a Debian Linux platform but requires zero Linux knowledge to use. All interaction with RAIDfinder is performed via a series of .txt files from a Windows network share.
Important Note: RAIDfinder works well on most NAS devices and other RAID arrays that use software RAID, where RAID meta-data is stored on each RAID member drive. Hardware RAID recovery is possible but requires manual operation.
Free to Use:
RAIDfinder is free for non-commercial use. For commercial use RAIDfinder is free to try but requires a key to access your recovered data.
Requirements:
A 64-bit computer with 2GB of memory and ideally with gigabit networking or USB-3 ports to copy recovered data at a high speed.
A wired network cable connected to a DHCP capable network with Internet accesss. Wireless will not work.
Safety:
RAIDfinder makes no changes to your RAID member drives. The drives are both write-protected and accessed read-only.
Operation:
Download the RAIDfinder .iso file and boot it on a computer with your RAID member drives attached.
Or if you are using image files, label the partition containing the images with the string “RAIDfinder” and it will be auto-mounted for use.
Optionally you may also attach a drive with a partition labeled “CopyDataHere” if you want RAIDfinder to copy recovered data.
After RAIDfinder boots it will display the path to a Windows network share.
Then simply go to a Windows computer and access the network share to see the info and action files and operating folders:
| Info Files | Description |
|---|---|
| info-start-here.txt | This file. |
| info-status.txt | Shows the current RAIDfinder state. Refresh often for updates. |
| info-smart.txt | Shows the S.M.A.R.T status of your drives, if possible. |
| info-system.txt | Shows info about the computer running RAIDfinder…including weather! |
| info-disk.txt | Shows both disk and partition views. Use this info before editing helper.txt. |
| Helper File | Description |
|---|---|
| helper-example.txt | Is an example of a RAIDfinder config file. Edit and rename to helper.txt to auto-launch a scan for RAID data. |
| Success File | Description |
|---|---|
| S_U_C_C_E_S_S.txt | Appears when RAIDfinder succeeds in recovering data. And contains instructions to proceed with the recovery. |
| Action Files | Description |
|---|---|
| action-request-key.txt | If RAIDfinder recovers your data enter your name and email to request a key. |
| action-copy-data.txt | Optional. Edit to launch a copy process of recovered data to a partition you’ve labeled: CopyDataHere |
| action-open-chat | Optional. Run to open a chat session with Stephen in your web browser. |
| action-allow-remote-help | Optional. Edit to permit Stephen to connect remotely to your RAIDfinder instance. |
| Folders | Description |
|---|---|
| RAIDfinder | Main control folder for RAIDfinder. |
| DataStructure | Appears when data is recovered. Contains a shadow copy of file and folder structure. Files are zero bytes. |
| Data | Appears when your key is approved. Contains your actual recovered data. See action-request-key.txt |
| DataCopied | Appears when data is copied to “CopyDataHere” partition. Contains data as it’s copied. See action-copy-data.txt |
| Spare | Will contain your image files from a partition labeled “RAIDfinder”, only if you are recovering from images. |
Limitations:
The current version supports 3, 4, 5 and 6 drive RAID sets using either RAID0, RAID1, RAID5 or RAID6. Support for larger RAID sets is planned.
File systems supported are Linux XFS BTRFS EXT2/3/4 with or without LVM and NTFS. Support for other file systems is planned.
Known Issues:
RAIDfinder can not handle chunk sizes smaller than 4096 bytes. This affects some Apple Mac RAID devices which use a 512 byte chunk.
RAID devices that use delayed parity are not supported such as HP Smart Array.
RAIDfinder can not recover Windows Dynamic disks but it is possible to recover with remote assistance.
DISCLAIMER:
The Software is provided “AS IS” and “WITH ALL FAULTS,” without warranty of any kind, including without limitation the warranties
of merchantability, fitness for a particular purpose and non-infringement. The Licensor (Stephen Haran) makes no warranty
that the Software is free of defects or is suitable for any particular purpose.
In no event shall the Licensor be responsible for loss or damages arising from the installation or use of the Software, including but not limited to
any indirect, punitive, special, incidental or consequential damages of any character including, without limitation, damages for loss of goodwill,
work stoppage, computer failure or malfunction, or any and all other commercial damages or losses. The entire risk as to the quality and performance
of the Software is borne by you. Should the Software prove defective, you and not the Licensor assume the entire cost of any service and repair.
………Below applies to single drive data recovery only…………
It’s possible to guide you through a do-it-yourself data recovery operation instead of using my remote data recovery service. That is to say you execute by hand all data recovery command operations but with my coaching. In this way you retain full control. And since there is no remote control of your computer using the do-it-yourself method is totally safe and secure. Note this DIY service applies only to single drive recovery due to the complexities of RAID recovery work.
I’ll give you all the steps you need to take from start to finish. This will include the software to use (all free open source software) and the commands to execute along the way. We will communicate via email, chat, and/or voice. Now this is not the quickest or most efficient option but it is the most secure option. It will take a bit more effort on your end but it is certainly workable and a great learning experience. So if you are extra cautious and prefer to perform a do-it-yourself data recovery without giving anyone control of your computer then complete the steps below to create your data recovery environment then shoot me an email and I’ll reply with further instructions.
Please note for any recovery attempt using software tools to be successful, at a minimum, your drive must be detected as present by your computer. For example, if you dropped your drive onto the floor and your computer no longer sees the drive then there is no software based data recovery solution that can help you.
Creating the DIY data recovery environment
First know that you will need two computers. Computer number one, the target computer, will act as a temporary data recovery workstation. It will have your failing hard drive connected to it. The second computer should be a standard Windows computer. We will use it as a communications console.
On the computer you have selected to use as your communications console install PuTTY. You will use PuTTY to remotely connect to the target computer.
https://putty.org/
All data recovery commands are executed from the Linux command line inside your PuTTY terminal window. So to get you familiar read up on Linux command line basics here’s one of many guides available on the net.
https://community.linuxmint.com/tutorial/view/100
Congratulations! You have just created your DIY data recovery environment and gained a little bit of Linux knowledge. Contact me for additional info and to arrange a time for us to begin the data recovery process.
Read MoreNetwork Share Creator
Turn any computer into a file server…Instantly!
Network Share Creator is a boot CD that exports all the partitions of the host computer as read-only network shares. Which can then be accessed by another computer on the same local network. It can be used for basic data recovery or just an easy way to transfer files. It is an alternative to the “hard drive slaving” process traditionally used to access data from a non-working computer. And may also prove useful to providers of remote technical support when operating on non-working computers. Note Windows FAT and NTFS, Mac HFS and HFSPlus, Linux EXT and XFS partition types are supported. But RAID arrays and NAS devices are not supported.
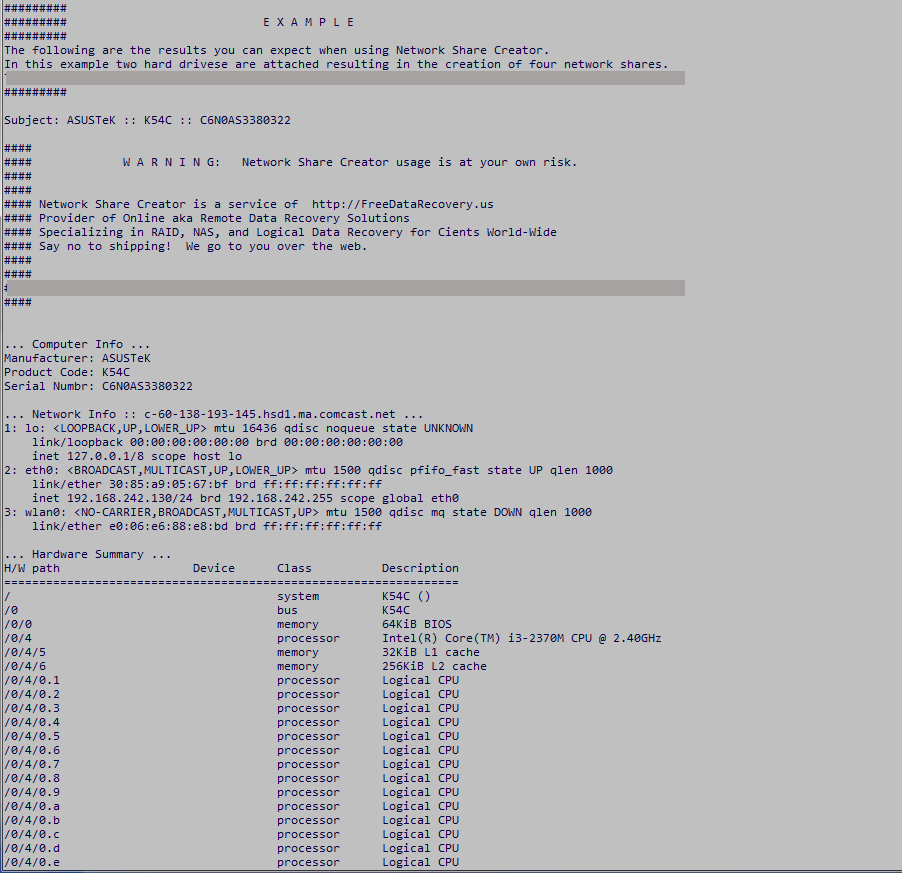
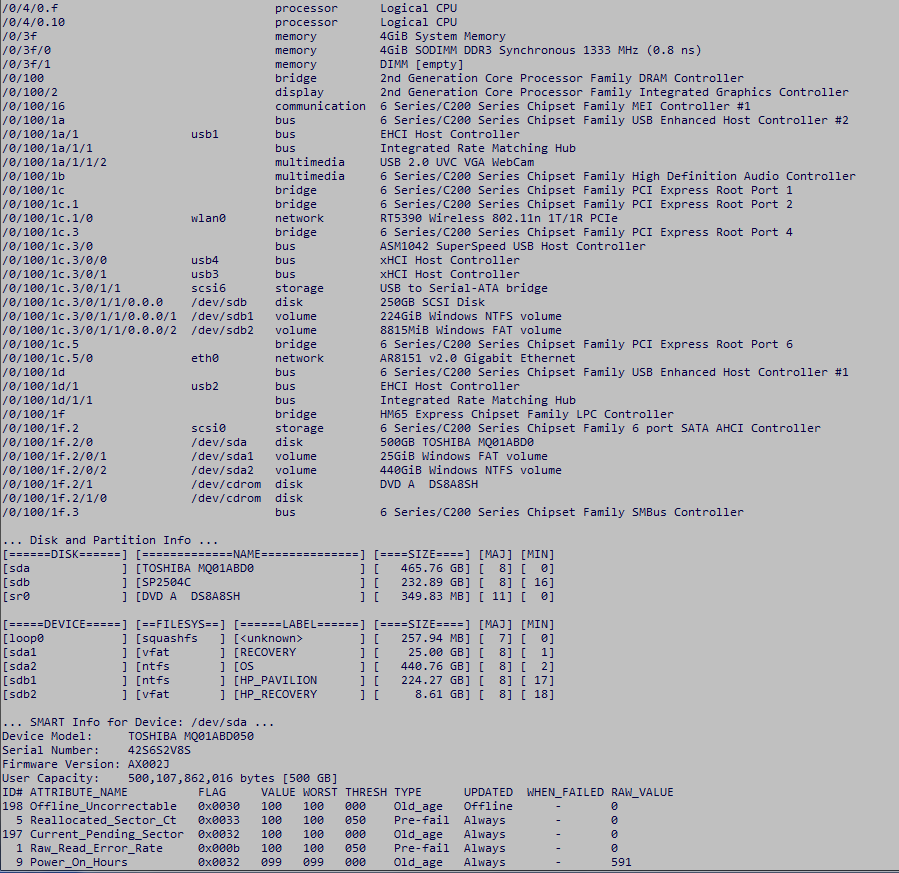
As part of the Network Share Creator process a report is generated containing a hardware summary, network settings, hard drive SMART data, partitioning info, etc. Note no personal data is collected. Reports are automatically uploaded and available for viewing by anyone here… https://FreeDataRecovery.us/nsc
How it works…
Network Share Creator basically automates the installation of a Samba file server that runs on top of the popular SystemRescueCD which is a Linux boot CD. It’s all Linux based but please know that zero Linux knowledge is required to use Network Share Creator.
Here are the instructions you need to get started. But first be aware that the hard drive you wish to share must be mechanically and electrically sound. If it is making unusual noises or if perhaps it was dropped or is otherwise damaged then do not use Network Share Creator.
0. Usage of Network Share Creator is completely at your own risk. And in corporate settings may go against security policy. Get the approval of your network admin before proceeding.
This program is distributed in the hope that it will be useful, but WITHOUT ANY WARRANTY expressed or implied, including the implied warranties of MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE.
1. Download the iso image file to make a bootable SystemRescueCD. You can get it here… https://www.sysresccd.org/Download
2. Burn the iso to a blank CD. Or better create a bootable USB flash drive with LiLi. You can get LiLi here… https://www.linuxliveusb.com
3. Boot the non-working computer with SystemRescueCD
4. From the blue SystemRescueCD start menu press the down arrow on your keyboard to highlight menu item B) or C) and press enter
5. On the next blue menu screen select menu item 1. and press the TAB key to edit boot options
6. At the end of the boot options line add a space and the 42 character string: ar_source=http://54.253.10.20/auto
7. Here’s how the full boot options line should look:
.linux rescue64 initrd=initram.igz ar_source=http://54.253.10.20/auto
8. Press enter
9. The SystemRescueCD starts to boot up with the Network Share Creator option enabled
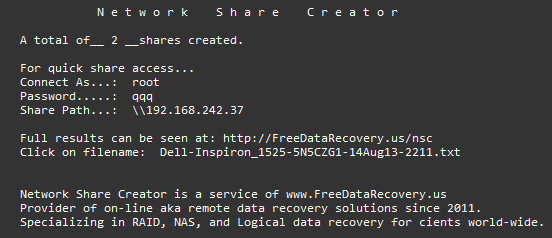
10. Wait two minutes for the finish message to appear. It will look similar to this…
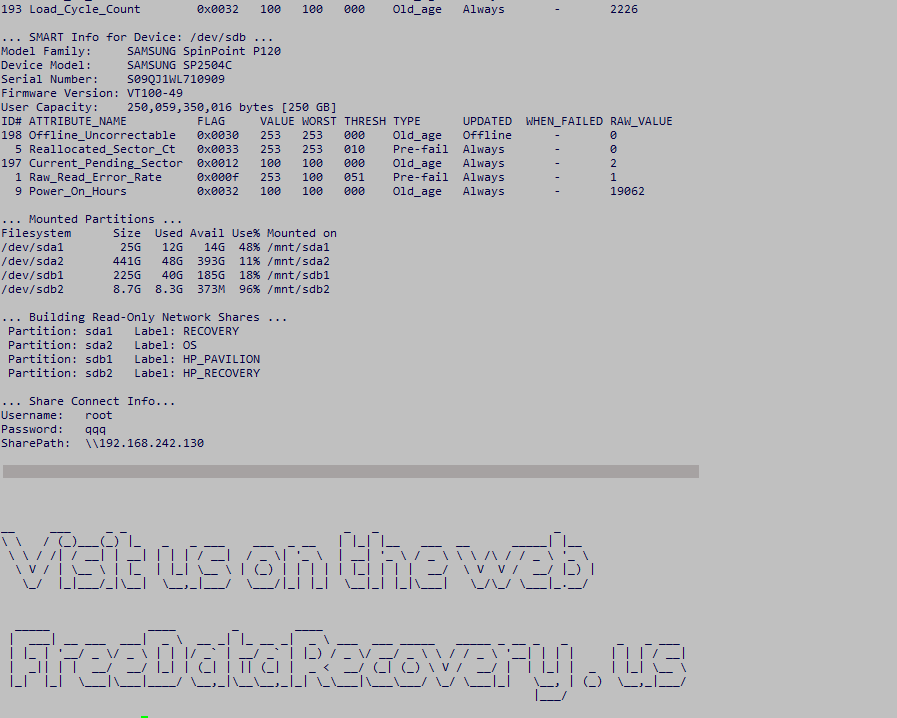
A real world example…
Below is an example of a report created by Network Share Creator. The report contains various pieces of system information but none is of a personal nature. Note the “…Share Connect Info…” section near the end contains the info you need to access the shares (username, password, and share path).
Accessing the shares…
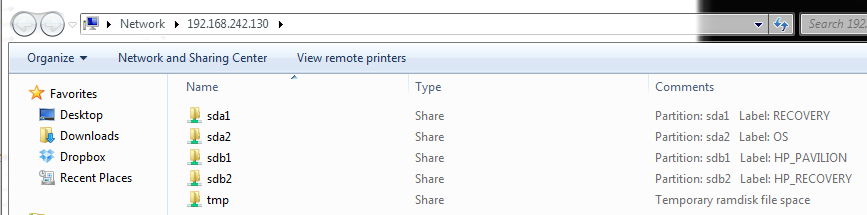
Now using the provided username, password, and share path you can access the shares from another computer on the same local network. Here is how the shares appear under Windows Explorer. Note the shares are not named with drive letters. Linux does not know drive letters. So you will see the standard Linux partition naming convention sda1, sda2, etc. But to help you identify things the partition label is shown under the “Comments” column inside Windows Explorer. Also note the tmp share contains a text copy of the full report generated by Network Share Creator.
Notes…
1. The target computer must be connected to the Internet via a local lan using a network cable. No wireless.
2. The local lan must be DHCP capable. (Most are.)
3. For security the local lan must use private, non-routeable ip addressing. (Most do.)
4. In the current version all network shares are created read-only.
5. If there are multiple nic’s on the target computer you must use the primary, ie. first nic port.
6. If this is something you use frequently it is possible to make a fully automated version with no boot option editing that sends mail directly to your email address.
7. And if you like Network Share Creator you want to check out a sister product called SysInfoByMail… https://www.SysInfoByMail.com
8. Comments and questions are most welcome.
Read More
Recent Comments